Instant Event Log Insight
Analyse Windows Event Logs using best practices suggested by Microsoft and the NSA with a focus on security, reliability and error reporting.

Understand Windows with better Event Log analysis. (1:39)
LogViewPlus has built-in reports to help you analyze your Windows Event Logs and EVTX files. Core reports show issues over time, user logins, system updates and more. Get valuable insights into system health and security with zero application configuration.
Windows Event Context
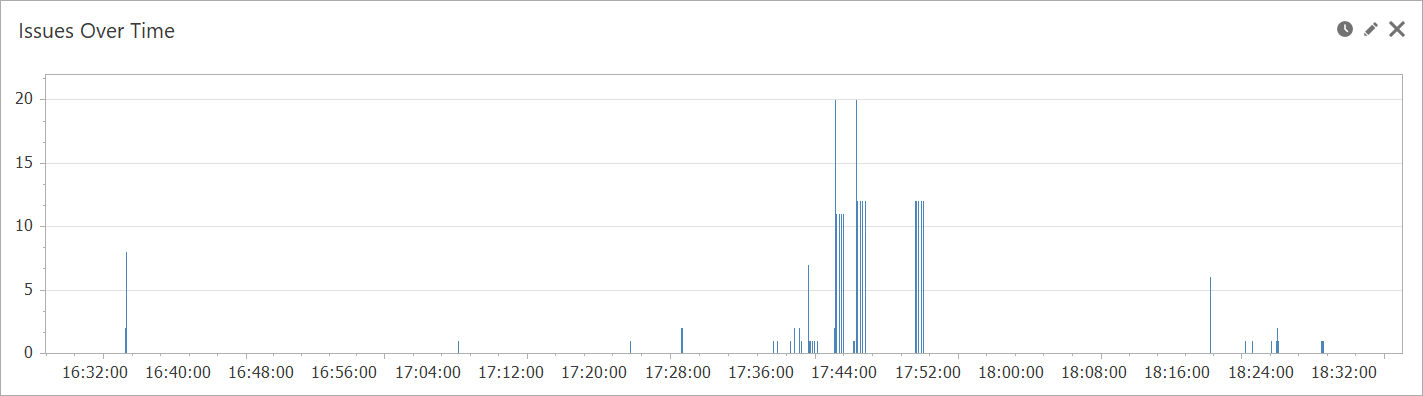
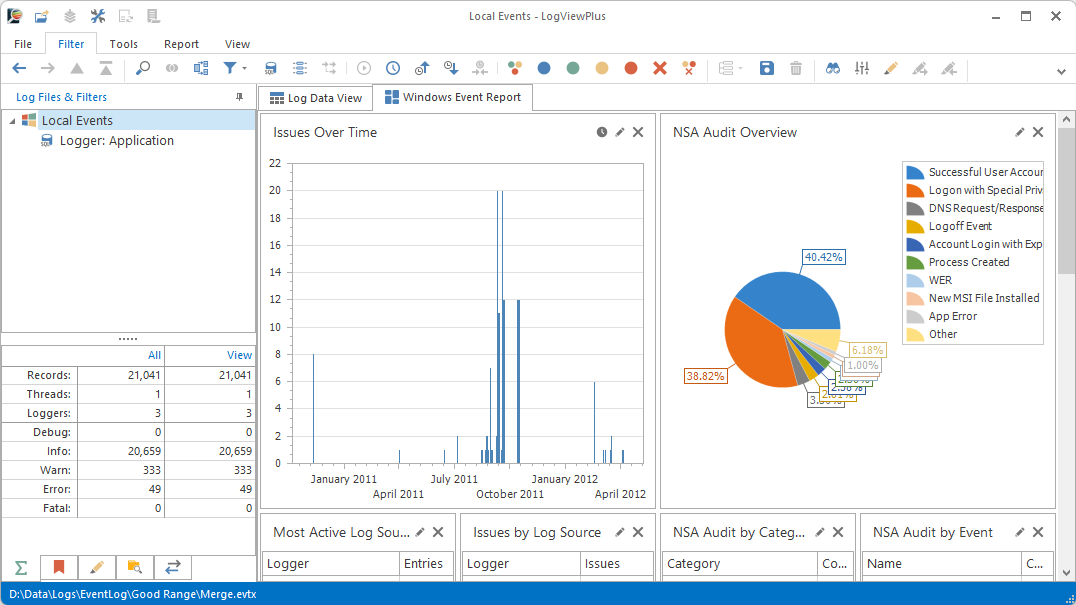
The first reports you see after opening a Windows Event Log or EVTX file contain an overview of all the issues which have occured in the time period and list the most active log sources. These reports provide context that can be important for understanding the nature of the audited activity. For example, events occuring late in the evening or an active securty log may be an indication of a hacking attempt that requires further analysis before considering other audit events.
Issues Over Time
SELECT CAST(Timestamp AS smalldatetime) AS Time,
COUNT(*) AS Issues
FROM CurrentView
WHERE Level in ( 'WARN', 'ERROR','FATAL')
GROUP BY CAST(Timestamp AS smalldatetime)
ORDER BY Time
In-Depth Log Analysis
LogViewPlus is not an enterprise Windows Event Log solution because it provides no centralized data storage. Instead, LogViewPlus reads events directly from a log source and adds value by providing a more in-depth analysis than most enterprise solutions. All of our prebuilt reports work out of the box with minimal configuration and support the ability to drill-down into the data. LogViewPlus is a full featured log analysis tool and reporting is just one of many features you can use to better understand your Windows Event Logs.
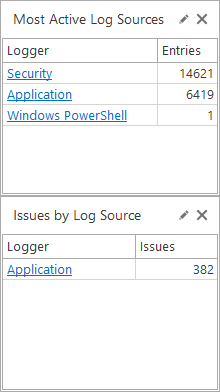
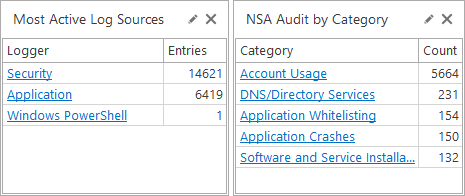
Most Active Log Sources
SELECT TOP 5 Logger, COUNT(*) AS Entries
FROM CurrentView
GROUP BY Logger
ORDER BY COUNT(*) DESCIssues by Log Source
SELECT TOP 5 [Logger], COUNT(*) AS Issues
FROM CurrentView
WHERE LEVEL in ('WARN', 'ERROR', 'FATAL')
GROUP BY [Logger]
ORDER BY Issues DESCNSA Cybersecurity Directorate Audit
The NSA Cybersecurity Directorate maintains a repository of event forwarding guidance including a list of recommended events to monitor. With LogViewPlus you can scan your Windows Event log file for matching events and quickly generate reports which help you maintain a healthy Windows environment. The NSA recommends monitoring over two-hundred separate events, so it really helps to have this automated. LogViewPlus offers a low cost, easy alternative to more expensive enterprise solutions. Perfect for small businesses or individuals looking to improve Windows security or reliability.
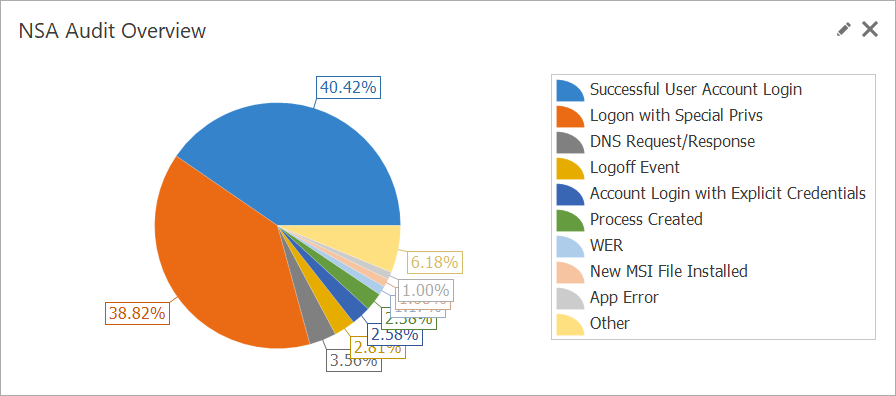
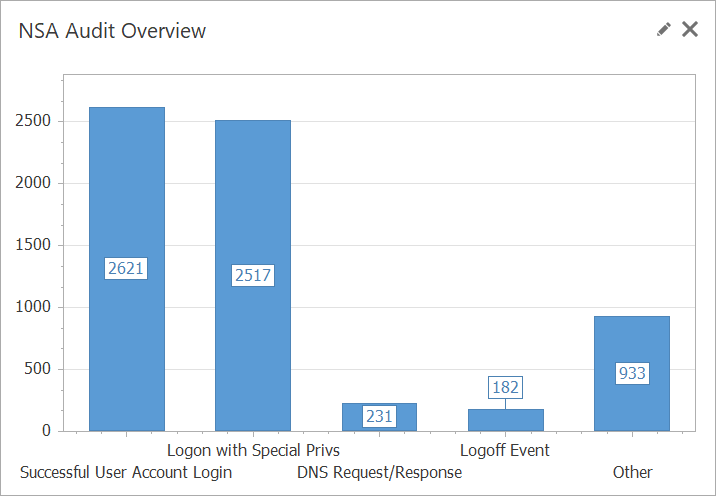
NSA Audit Overview
select CASE WHEN RowNumber > 9 THEN 'Other'
ELSE Description END AS Description,
SUM(Count) AS Count
FROM (
SELECT W.Name AS Description, COUNT(*) AS Count,
ROW_NUMBER() OVER(ORDER BY COUNT(*) DESC) AS RowNumber
FROM CurrentView AS C
JOIN LoadCsv('NSA Windows Event Categories.csv')
AS W ON W.id=C.Id
GROUP BY W.Name
) AS qry
GROUP BY CASE WHEN RowNumber > 9 THEN 'Other'
ELSE Description ENDNSA Audit Drill Down
LogViewPlus uses SQL to combine your Event Log data with the enriched event data provided by the NSA, offering a powerful and flexible approach to log analysis. By leveraging SQL queries, users can create personalized reports that show important trends, patterns, and security risks, helping you quickly find and focus on the most important issues. Adding NSA data gives more context to each event, giving you a better overall view of security. This method makes it easier to understand your logs and helps you make better decisions with more detailed information.
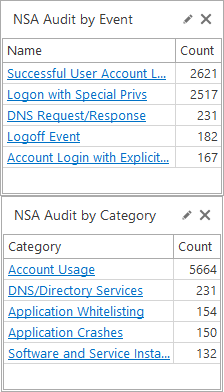
NSA Audit by Event
SELECT TOP 5 W.Name, COUNT(C.ID) AS Count
FROM CurrentView AS C
JOIN LoadCsv('NSA Windows Event Categories.csv')
as W on W.id=C.Id
GROUP BY W.Name
ORDER BY Count DESCNSA Audit by Category
SELECT TOP 5 W.Category, COUNT(C.ID) AS Count
FROM CurrentView AS C
JOIN LoadCsv('NSA Windows Event Categories.csv')
as W on W.id=C.Id
GROUP BY W.Category
ORDER BY Count DESCMicrosoft Event Log Audit
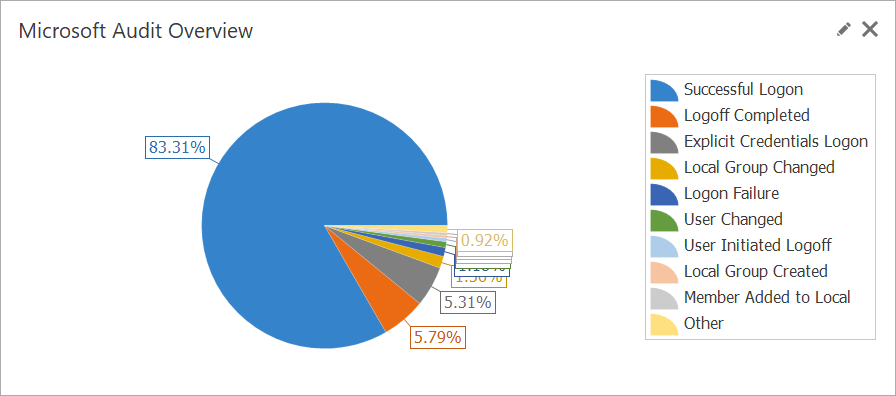
LogViewPlus can also monitor Windows Event Logs in line with Microsoft's security audit policy settings. These settings help maintain a secure environment by monitoring various types of activities such as user logons, account management actions, access to Active Directory, folder accesses, policy changes, privilege use, process tracking, and system-related events like restarts or shutdowns. By adhering to these guidelines, the program can check for critical security events and help you detect potential security threats and address vulnerabilities before they can be exploited.
Microsoft Audit Overview
SELECT CASE WHEN RowNumber > 9 THEN 'Other'
ELSE Description END AS Description,
SUM(Count) AS Count
FROM (
SELECT M.Description AS Description, COUNT(*) AS Count,
ROW_NUMBER() OVER(ORDER BY COUNT(*) DESC) AS RowNumber
FROM CurrentView AS C
JOIN LoadCSV('Microsoft Audit Events.csv')
as M on M.Id = C.Id
GROUP BY M.Description
) AS qry
GROUP BY CASE WHEN RowNumber > 9 THEN 'Other'
ELSE Description ENDEvent Log Drill Down
LogViewPlus let's you dive into the data. This helps you understand how multiple events are related and can help in piecing together the narrative behind security incidents or system anomalies. Multiple features combine to facilitate a deeper understanding of issues that might not be apparent from isolated events. Consequently, administrators are equipped with the necessary information to make faster, more informed decisions. This holistic view of events not only accelerates the troubleshooting and resolution process but also significantly enhances the ability to address potential issues.
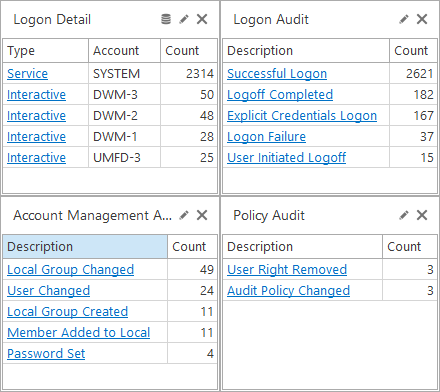
Logon Detail
SELECT TOP 5 T.LogonTitle AS Type, C.Account, COUNT(*) AS Count
FROM CurrentView AS C
JOIN LoadCSV('Logon Types.csv') AS T
ON T.LogonType = C.LogonType
GROUP BY T.LogonTitle, C.Account
ORDER BY Count DESCPolicy Audit
SELECT TOP 5 M.Description AS Description,
COUNT(*) AS Count
FROM CurrentView AS C
JOIN LoadCSV('Microsoft Audit Events.csv') AS M on M.Id = C.Id
WHERE M.Category = 'Policy Change'
GROUP BY M.Description
ORDER BY Count DESCExplore with SQL
LogViewPlus uses a custom SQL engine based on Transact-SQL which makes it is easy to transform your data. The SQL engine works with the parsed log entry data already in memory. So query execution is super fast while avoiding the need to put your data into another system. Fast query execution based on a standard query language makes LogViewPlus a great tool for exploring your logs to gain new insight.
Account Management Audit
SELECT TOP 5 M.Description AS Description,
COUNT(*) AS Count
FROM CurrentView AS C
JOIN LoadCSV('Microsoft Audit Events.csv') AS M on M.Id = C.Id
WHERE M.Category = 'Account Management'
GROUP BY M.Description
ORDER BY Count DESCDirectory & Privilege Audit
SELECT TOP 5 M.Description AS Description,
COUNT(*) AS Count
FROM CurrentView AS C
JOIN LoadCSV('Microsoft Audit Events.csv') AS M on M.Id = C.Id
WHERE M.Category = 'Privilege Use'
OR M.Category = 'Directory Service'
GROUP BY M.Description
ORDER BY Count DESCBest of all, you are in control.
LogViewPlus has some prebuilt reports, but these are just the start. With custom SQL and quick charting built-in, you can explore your Windows Event Logs any way you want. Check out our documentation for more information about creating custom reports.
Plus tons of other useful features!
LogViewPlus can help you with a lot more than just Windows Event Logs. LogViewPlus is a full featured log file analysis program. Check out some of our other great features in our short video tutorials.






















Level up your log files in 2 minutes.
See how we can help you read and analyze log files with our free trial.