Windows Events
LogViewPlus can use a Windows Event connection to read event log entries directly from a local or remote machine.
When reading log entries in Windows, there are two important security settings that you may need to modify.
1. To access the local Security log, LogViewPlus must be running under the administrator account.
2. If you are trying to connect to a remote server make sure that the "Remote Registry" service is running and that the user account you are trying to connect with is a member of the "Event Log Readers" group. The "Administrator" group is not needed and will not work.
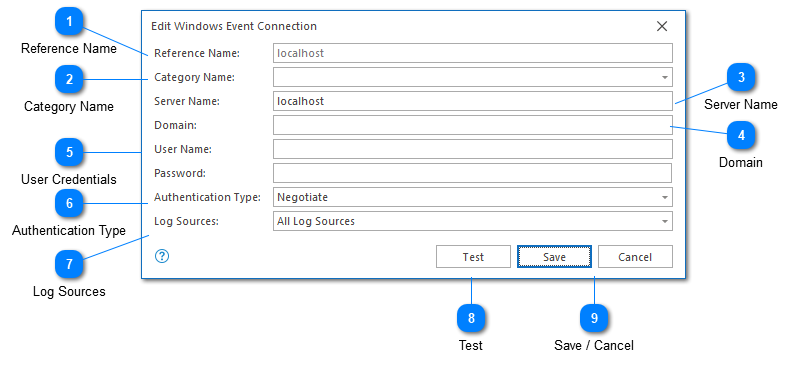
Reference Name
A reference name can be set to more easily manage and access this configuration. Reference names should be unique. By default, the reference name will mirror the server name. Reference names are also be used by the local log level and automatic template settings.
The name provided will be used to build a URI which can be used to refer to this server. For this reason, the name provided must be URI friendly - it should not contain characters or symbols which are difficult to represent in URI form.
Category Name
A category name is used to group Syslog connections into a folder in the Log Explorer. This field is not required.
If you have previously configured a server with a category name, this name will be available as a drop-down option. Alternatively you can type a new name into the category text box.
Server Name
The name of the server which is hosting the Event Logs we want to access. This can either be a host name or an IP address.
Domain
The domain of the specified user. This field will be used when connecting to remote machines.
User Credentials
The user credentials which should be used when monitoring the event logs. This field can be left blank to use the current user credentials. Note that the user name should be provided without the domain prefix. The domain prefix will be supplied by the 'domain' field discussed above.
If you want to log in using your current security context instead of a user name and password, please leave the user name field blank.
Authentication Type
The type of authentication to use. The values presented are adapted from the SessionAuthentication enumeration.
Log Sources
The log sources you want to monitor.
The list of log sources is extracted dynamically from the target machine. If you do not see a log source you are interested in accessing, this may be due to permissioning issues. Make sure that LogViewPlus is running under the correct user account.
Test
Validates and tests the provided configuration.
Save / Cancel
Once you have configured your server, you can use the save command to persist your changes. Once your changes have been saved the configured server will be immediately available in the folder tree view.
Use the "Cancel" command to return to LogViewPlus without saving your changes.